An Expert Analysis of Google Password Manager's Security
The challenge of creating and remembering dozens of complex credentials has led to the rise of password managers. While many opt for dedicated third-party applications, millions rely on the convenience of password managers built directly into their web browsers.
Google Chrome, which as of mid-2025 maintains a global market share of over 65% according to Statcounter, includes a free, deeply integrated password manager. Its seamless nature simplifies logins across desktops and mobile devices, making it an accessible choice for a vast user base.
This convenience, however, prompts a critical evaluation: How secure is entrusting your entire digital key-ring to Google's ecosystem? This article provides a comprehensive, neutral analysis of the Google Password Manager's architecture, its security strengths and weaknesses, and how it compares to specialized, dedicated solutions.
Table of Contents
How Google Password Manager Functions
Understanding the security of Google's offering begins with how it handles your data.
When you save a credential in Chrome, it is encrypted and stored. The security of this process relies on two distinct stages:
-
Encryption in Transit: When your passwords sync between your devices and Google's servers, they are protected using Transport Layer Security (TLS), the standard cryptographic protocol that secures internet communications.
-
Encryption at Rest: On Google's servers, your passwords are encrypted using Advanced Encryption Standard (AES), a robust, industry-standard algorithm. The encryption keys used to secure this data are themselves stored securely by Google.
Crucially, the accessibility of your passwords is tied directly to your Google Account authentication. When you are logged into your Google Account in Chrome, the browser can decrypt and use your saved credentials. This single-login convenience is the system's core design principle and its most significant point of security consideration.
Security Strengths: A Powerful Starting Point
For the average user, Google Password Manager offers a significant security upgrade over common, insecure practices like password reuse or storing credentials in a simple text file.
-
Accessibility and Cost: It is free and pre-installed in the world's most popular browser, removing barriers to adoption. This accessibility encourages better basic password hygiene for millions of users.
-
Strong Core Encryption: Google utilizes industry-standard AES encryption, providing a strong technical foundation for data protection on its servers.
-
Seamless Integration: It integrates with Google's broader security ecosystem. This includes security alerts for compromised passwords found in data breaches and prompts to change weak or reused credentials.
-
Password Generation: The built-in generator helps users create strong, randomized passwords for new accounts, preventing the creation of weak or easily guessable credentials.
Key Security Weaknesses and Risks
While beneficial, the architecture of Google Password Manager presents inherent risks that differ from those of dedicated password managers.
1. The "Single Point of Failure" Model
The most significant risk is that the security of your entire password vault is synonymous with the security of your Google Account. If an attacker gains unauthorized access to your Google Account through methods like phishing, malware, or credential stuffing, they gain access to every password you have saved.
2. The Absence of a True Master Password
Dedicated password managers typically require a unique "master password" that is known only to the user and is never transmitted to the provider. This password decrypts the vault locally on your device. Google Password Manager does not use this model by default. Instead, your Google Account password (and your multi-factor authentication) serves as the key. This conflates the key to your email, cloud storage, and photos with the key to your entire password vault.
3. A Lack of Zero-Knowledge Architecture
This is a fundamental differentiator. Most leading dedicated password managers are built on a "zero-knowledge" principle. This means your data is encrypted and decrypted locally on your device using your master password. The service provider only ever stores the encrypted "blob" of data and has no way to decrypt it.
Google, by contrast, manages the encryption keys tied to your account. This design allows for features like password recovery if you forget your Google password. However, it also means that, under certain circumstances (such as a valid law enforcement request or compromise by a sophisticated attacker or malicious insider), Google possesses the technical capability to decrypt a user's passwords.
Threat Models: How Your Passwords Could Be Compromised
Understanding the specific ways your vault could be breached is essential for proper risk assessment.
-
Google Account Takeover: This is the most probable threat. An attacker who successfully phishes your Google credentials can log in from their own device and access
passwords.google.com, revealing your saved information. -
Compromised Device: If your computer or phone is infected with information-stealing malware, the malware can be designed to exfiltrate the locally stored password database from Chrome.
-
Unauthorized Physical Access: If you leave your device unlocked and logged in, a person with physical access can potentially navigate to Chrome's settings and view saved passwords, often only needing your device's PIN or password for verification.
A Crucial Security Step: Enabling Sync Passphrase
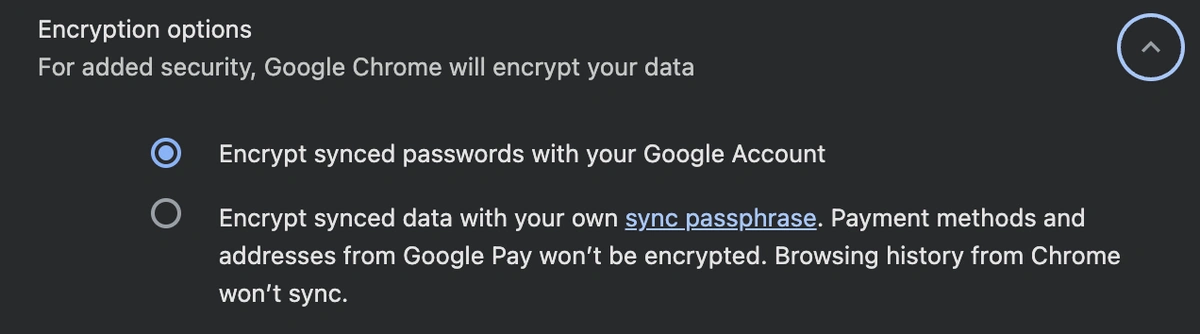
To its credit, Google offers a feature that significantly mitigates some of these architectural weaknesses: the ability to set a sync passphrase.
When enabled, this option adds a second layer of encryption to your synced data (including passwords) using a passphrase that you choose. This passphrase is not stored by Google.
-
How it Works: Your data is still synced through Google's servers, but it remains encrypted with your unique passphrase. Google cannot decrypt this data without it. This effectively transforms the system into a model much closer to zero-knowledge architecture.
-
The Trade-off: If you forget this passphrase, your synced data cannot be recovered. You would need to reset the sync function, which would delete the data from Google's servers, and then re-establish your vault from one of your local devices.
To enable this, navigate to Chrome Settings > "You and Google" > "Sync and Google Services" > "Encryption options" and select "Encrypt synced data with your own sync passphrase."
Google Password Manager vs. Dedicated Managers
The choice between Google's solution and a dedicated manager depends on your personal threat model and desired features.
| Feature | Google Password Manager | Dedicated Password Managers (TeamPassword, LastPass) |
| Security Model | Tied to Google Account security. Not zero-knowledge by default. | Zero-knowledge architecture. Vault is secured by a separate master password. |
| Primary Risk | Google Account takeover compromises the entire password vault. | Forgetting the master password leads to permanent loss of access. |
| Cost | Free. | Typically require a paid subscription for full features. |
| Convenience | Highest. Built-in, seamless sync within the Google ecosystem. | High. Requires installation but offers browser extensions and apps for all platforms. |
| Advanced Features | Basic password generation and breach alerts. | Often includes secure notes, identity storage, digital legacy planning, and advanced security reports. |
| Team/Family Sharing | Basic password sharing with other Google users. | Robust and granular sharing options for families and business teams. |
Conclusion: A Capable Tool That Demands Diligence
Google Password Manager is not inherently insecure. It is a robust, convenient tool that provides a substantial security benefit for the average user, especially when compared to having no password management strategy. Its primary weakness is not its encryption but its architectural reliance on a single point of failure: the Google Account.
For users who choose Google Password Manager, security is an active responsibility:
-
Secure Your Google Account: Use a long, unique, and complex password for your Google Account.
-
Enable Multi-Factor Authentication (MFA): This is non-negotiable. Use a strong MFA method like an authenticator app or a physical security key.
-
Enable the Sync Passphrase: This is the single most important step to elevate its security, creating a barrier that prevents Google from being able to access your password data.
A dedicated password manager is the superior choice for individuals with a heightened threat model, those who manage sensitive business credentials, or anyone who prefers the "belt-and-suspenders" approach of a zero-knowledge system with a distinct master password. For them, the modest annual cost is a worthwhile investment for enhanced peace of mind and greater control over their digital security.
TeamPassword is built for simple, efficient security. Gain complete control and peace of mind with robust features designed for team collaboration:
-
Integrated TOTP Authenticator: Generate time-based one-time passcodes directly within TeamPassword, eliminating the need for separate authenticator apps on your phone.
-
Enforceable 2FA: Mandate two-factor authentication for every user across your organization, ensuring a consistent and high standard of security.
-
Detailed Activity Logs: Maintain full visibility with a complete audit trail of who accessed what and when, perfect for security audits and accountability.
-
Unlimited Records & Groups: Store an infinite number of logins and organize them into logical groups by team, project, or client for easy access and management.
-
Multiple User-Roles: Assign granular permissions to control exactly who can view, edit, and create credentials, ensuring access is granted only where it's needed.
-
Free Google Sign-In: Simplify onboarding and daily access with secure, one-click login using your team's existing Google accounts.
-
One-Time Share: Securely share a single password with an external contractor or partner for a limited time, without giving them permanent access to your records.
With straightforward plans starting at just $2.41 per user per month, TeamPassword is the most effective and affordable way to protect your business.